FinOps v7.0-Infrastructure Deployment Process
Contents
- Important Terms
- Overview
- Architecture
- Download the installation package in cloud shell
- Scripts location for Base Infra and Product Infra deployment
- ARM Templates for ase Infra and Product Infra deployment
- Install Base Infrastructure
- Install Product Infrastructure
- Post Deployment Validations for Infrastructure
- Az MYSQL Firewall policies
- Key vault permissions for the Azure AD user.
- Azure service principal needs Get permission to Key Vault secrets.
- Disk Encryption set, storage account, Azure MySQL instance’s Key permissions
- User’s access to Azure Key Vault instance
- Private Endpoint’s IP associations
- Node pools’ zone redundancy
- APPENDIX
- Known Issues during Infrastructure deployment and Resolutions.
- Issues
- Resolutions
- Private Endpoint IP of Azure MySQL, Storage accounts and key vault not associated with respective private link.
- Azure ARM template deployment failures with status ‘Operation Timed Out’. This can be resolved by redeploying the template.
- Azure ARM template deployment with status ‘CONFLICT’. This can be resolved by redeploying the template.
- File copying issues to Storage account blob containers because of firewall policy restricted to ‘all networks.
- Kubernetes cluster not able to access key vault because of not setting correct access policies
- Disk Encryption set not able to get the keys because of not having the Get Wrap and Unwrap permission to key stored in Azure Key Vault.
- Deployment Engineer not able to access Azure Key vault because of not having required access policies set in Azure Key Vault.
- Bad Request Status for Storage Account Resources.
- FAQ
Important Terms
|
Base Infra |
The base Infrastructure which needs to be created before deploying product Infrastructure |
|
Product Infra |
The Kubernetes infrastructure required for respective product |
Overview
Welcome to Kubernetes Infrastructure deployment guide for PWF IE 7.0. This document provides an overview of the flow of activities and overall architecture for installation of PWF IE 7.0
The main activities involved in this Kubernetes Infrastructure deployment guide is as below.
-
Base Infrastructure Installation in Azure Cloud
-
Installation and Configuration of Kubernetes Infrastructure for PWF Invoice Extraction
To get a deeper understanding about the installation read further about SmartOps 7.0 architecture.
Architecture
PWF IE 7.0 is a distributed cloud application. It can be installed only in cloud infrastructure. PWF IE 7.0 is deployed and managed in Kubernetes. Even though it is there in our roadmap to be cloud agnostic, at this point of time the installation is compatible and tested only on Microsoft Azure Cloud Infrastructure. Support for more cloud will follow in subsequent releases.
The below diagram provides an overview
< We need insert the latest architecture diagram here >
-
The installation is done on a single virtual network with multiple Subnets.
-
Each Subnets will be self-isolated with NSG rules and only required access granted. Each PWF and Platform will reside in its own Subnet.
-
Additionally, there will be a maintenance subnet where a bastion is hosted for administrative activities.
-
In certain situations, clients of SmartOps PWFs will have to get TCP connectivity to assets in SmartOps. For e.g. Posting data to a SmartOps Queue. In such cases as the diagram shows a VPN connectivity is established from client network to SmartOps Network. The connectivity is terminated at a DMZ subnet where a squid machine will isolate client network from SmartOps application subnets, for enhanced security.
Download the installation package in cloud shell
The Release packages are stored in SharePoint location and in azure artifacts. Please follow below steps for downloading the Azure Infrastructure installation scripts to Azure cloud shell.
-
Open Azure cloud shell
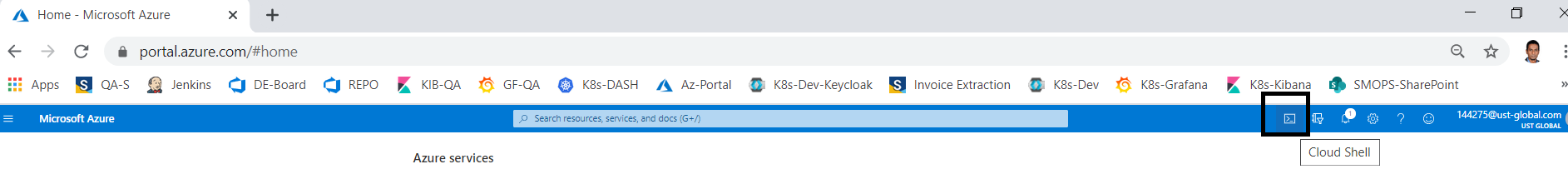
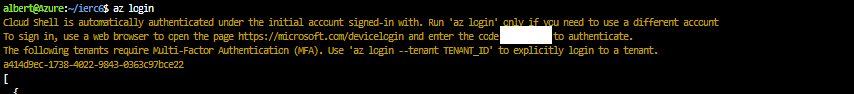
-
az login in cloud shell
-
The package downloaded from SharePoint has to be made available in Azure cloud shell
-
SharePoint location
-
-
After downloading the package in cloud shell scripts for deploying
Scripts location for Base Infra and Product Infra deployment
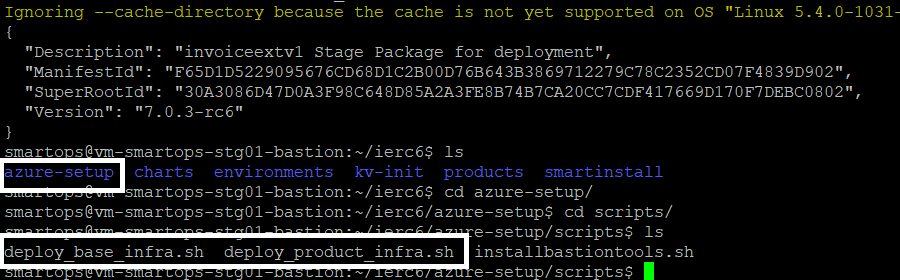
After package is downloaded, the scripts for installing base and product infra will be available in
<package_folder_name>/azure-setup/scripts folder
ARM Templates for ase Infra and Product Infra deployment
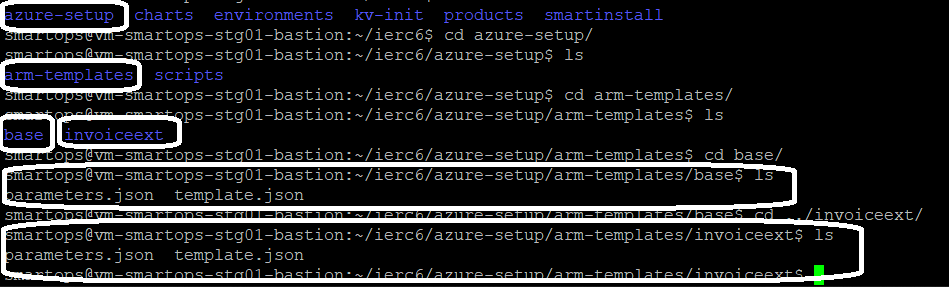
After package is downloaded, the scripts for installing base and product infra will be available in
<package_folder_name>/azure-setup/arm-templates folder.
Install Base Infrastructure
-
Once the package is downloaded, cd into <package_folder_name>/azure-setup/scripts folder.
-
Execute the shell script deploy_base_infra.sh in Azure cloud shell by passing required parameters
./deploy_base_infra.sh <subscription_id> <resource_group> <environment> <base_ip_seg> <smartops_domain_name> <sp_client_id> <tenant_id> <sp_client_secret>
Parameters
|
Parameter |
Description |
|
subscription_id |
Azure Subscription ID where base infra needs to be deployed |
|
resource_group |
Azure Resource Group where base infra needs to be deployed |
|
environment |
Environment Name. Restricted to maximum 5 characters. E.g.: dev02, stg01 |
|
base_ip_seg |
The base IP segment of the environment’s IP Range |
|
smartops_domain_name |
Can be left blank. DNS creation will be taken care by the ARM template. |
|
sp_client_id |
Azure Subscription Service Principal client ID |
|
tenant_id |
Azure subscription Tenant ID |
|
sp_client_secret |
Azure subscription client secret |
Base Infrastructure Deployment validation
Select Deployments in respective resource group and look for ‘basedeployment’ to check the status of base infrastructure deployment.

Install Product Infrastructure
-
Once the package is downloaded, cd into <package_folder_name>/azure-setup/scripts folder.
-
Execute the shell script deploy_product_infra.sh in Azure cloud shell by passing required parameters
|
./deploy_product_infra.sh <subscription_id> <resource_group> <environment> <product> <aksNodeImageVersion> <sp_client_id> <tenant_id> <sp_client_secret> <mysql_admin_password> |
Parameters
|
Parameter |
Description |
|
subscription_id |
Azure Subscription ID where base infra needs to be deployed |
|
resource_group |
Azure Resource Group where base infra needs to be deployed |
|
product |
Name of PWF or product. E.g.: invoiceextv1 |
|
aksNodeImageVersion |
OS Image version of K8s cluster. Recommened to be set latest. |
|
sp_client_id |
Azure Subscription Service Principal client ID |
|
tenant_id |
Azure subscription Tenant ID |
|
sp_client_secret |
Azure subscription client secret |
|
mysql_admin_password |
Admin password for the Azure MySQL instance |
Product Infrastructure Deployment validation
Select Deployments in respective resource group and look for ‘basedeployment’ to check the status of base infrastructure deployment.

Post Deployment Validations for Infrastructure
After successful deployments of base and product infrastructure using the shared ARM templates in the package, below validations needs to be performed before proceeding with the Application deployment.
|
#1 |
Az MYSQL Firewall policies |
|
#2 |
Key vault permissions for the Azure AD user |
|
#3 |
Azure service principal needs Get permission to Key Vault secrets. |
|
#4 |
Disk Encryption set, storage account, Azure MySQL instance needs GET, Wrap and Unwrap Key permissions. |
|
#5 |
User’s access can be enabled by Adding users with required set of permission to access key, secret and certificate which is listed under USER section |
|
#6 |
Private Endpoint’s IP associations |
|
#7 |
Node pools’ zone redundancy |
Az MYSQL Firewall policies
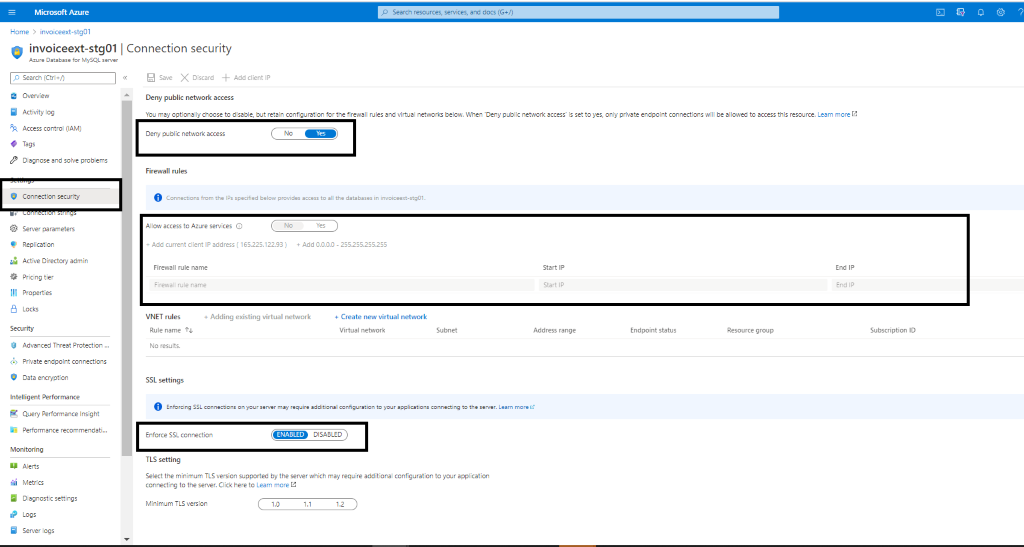
- Public network access should be denied.
- Allow access to Azure MySQL by configuring firewall policies
- Enforce SSL connection should be Enabled
Key vault permissions for the Azure AD user.
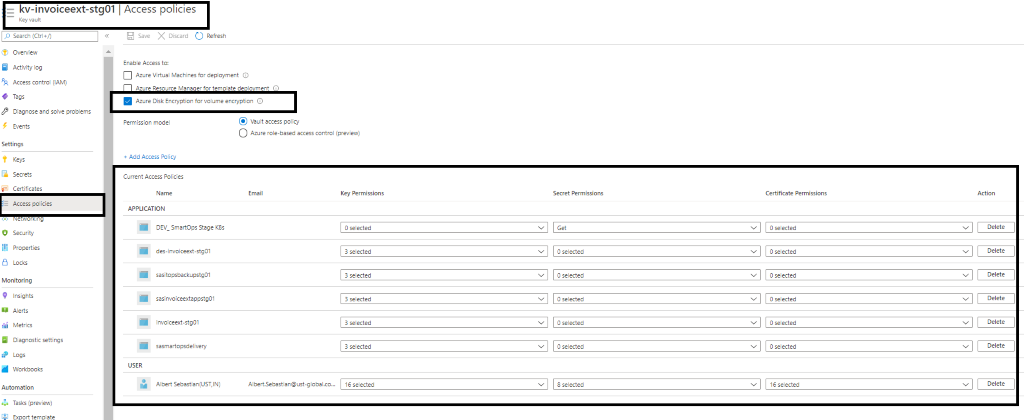
-
Access to key vault can be enabled by configuring Key Vault access policies.
-
Before proceeding with deployment, we need to validate
-
Access is enabled for Disk Encryption
-
Permission model set as Vault access policy
-
Respective applications and resources are added with required access under APPLICATION section
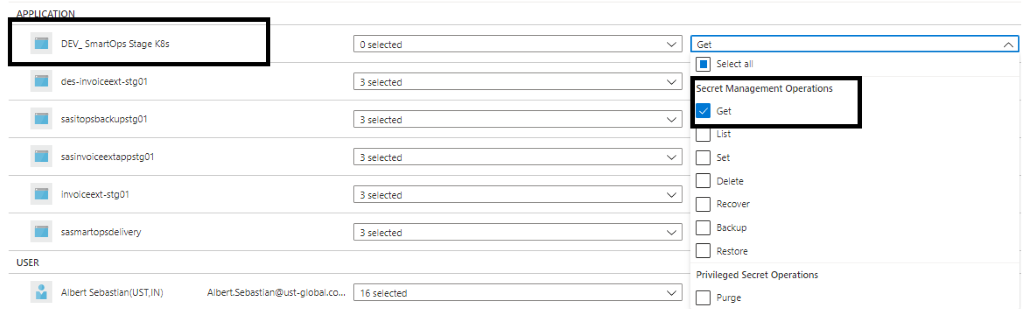
Azure service principal needs Get permission to Key Vault secrets.
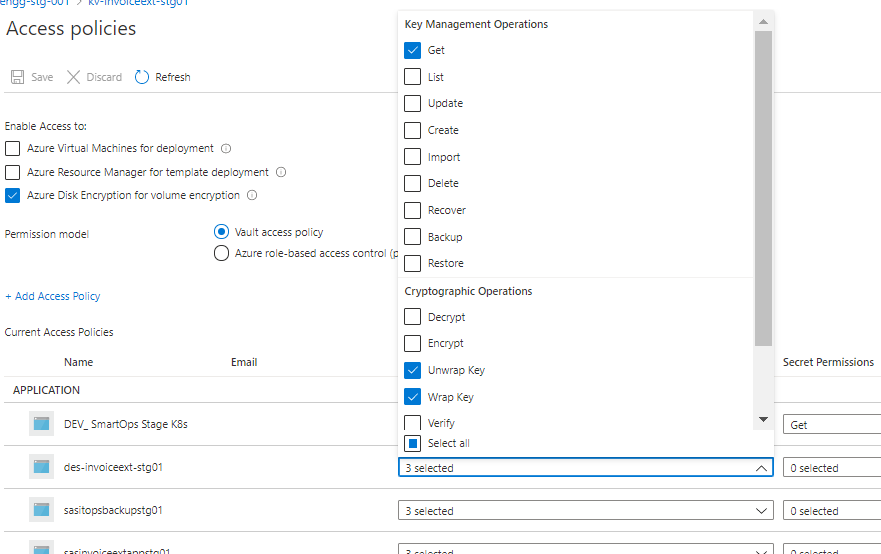
Disk Encryption set, storage account, Azure MySQL instance’s Key permissions
Disk Encryption Set, Storage Account and Azure MySQL instance needs Get, Wrap and Unwrap key permissions.
Please refer below example for disk encryption set.
User’s access to Azure Key Vault instance
User’s access can be enabled by Adding users with required set of permission to access key, secret and certificate which is listed under USER section .
Please refer below screenshot.
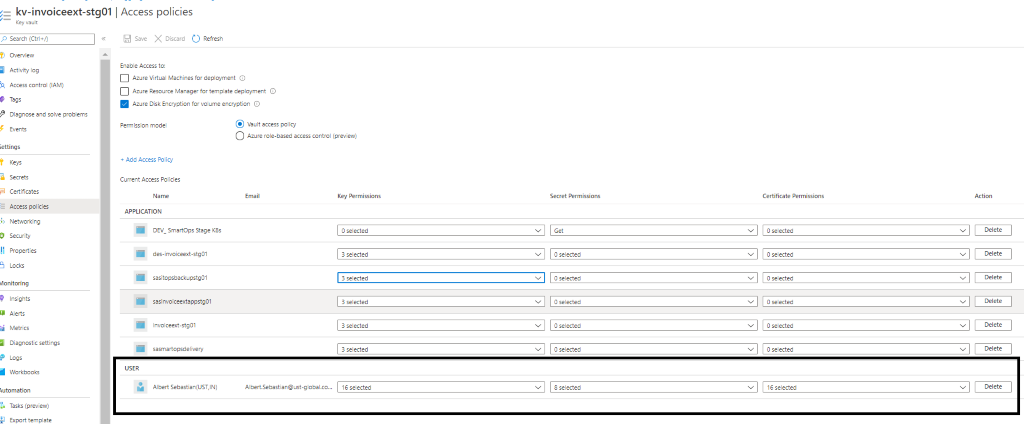
Private Endpoint’s IP associations
-
we have 4 private endpoints per environment. For these 4 private endpoints, we have 3 private DNZ zones. One private zone per Azure blob, Azure Key Vault and Azure MySQL instances.
-
There should be a private IP against each of these services. If this private IP is not associated to the respective private endpoints, application deployments will fail as the K8s cluster will not be able to communicate with these private endpoints. We must manually add it via Azure portal, if found not associated.
-
PFB screenshots for reference
Key Vault Private Endpoint and its Private IP
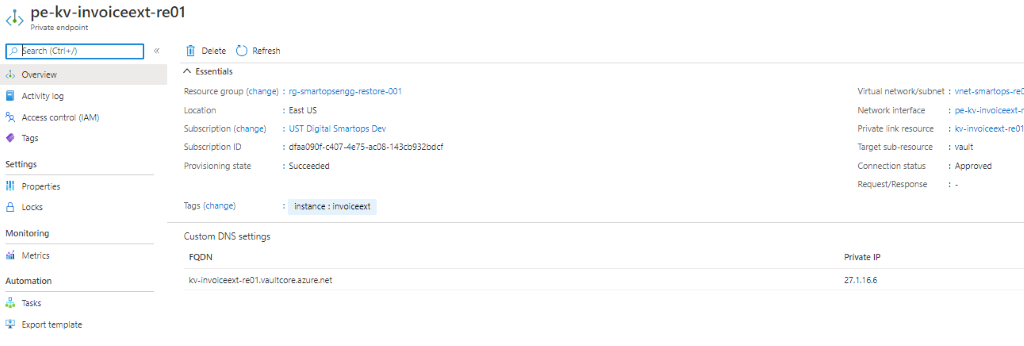
Above Key Vault’s Private IP associated with respective Private Link of Key Vault
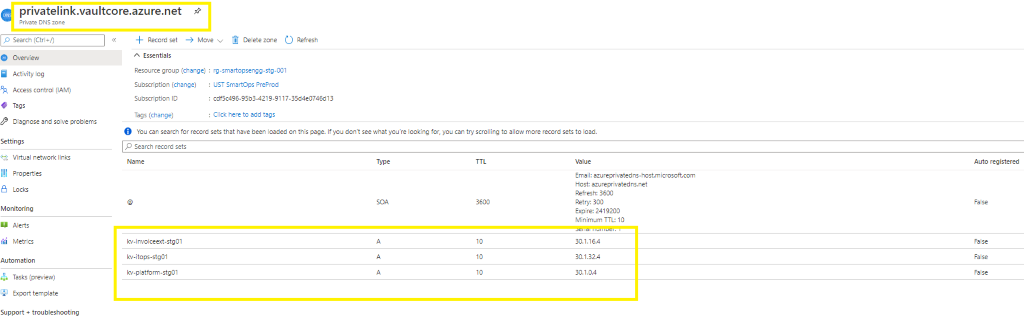
Update Private IP in Private Link
-
Please refer below screenshot when private endpoint’s IP is not associated with the private link.
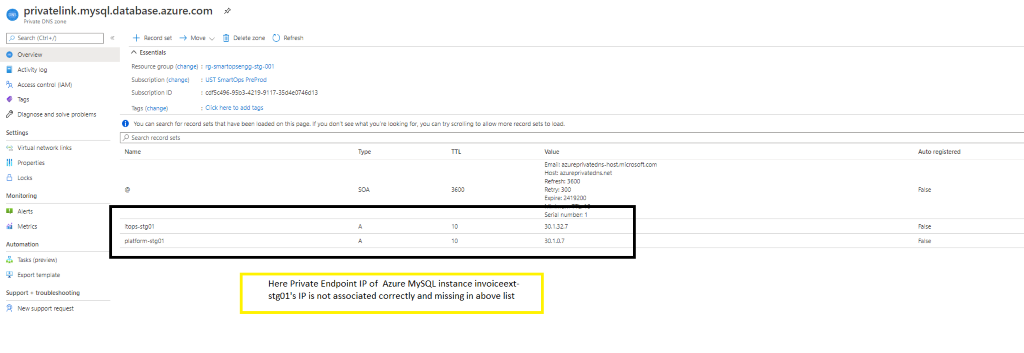
-
When private endpoint IPs are not listed, include the same by adding record set of respective resource.
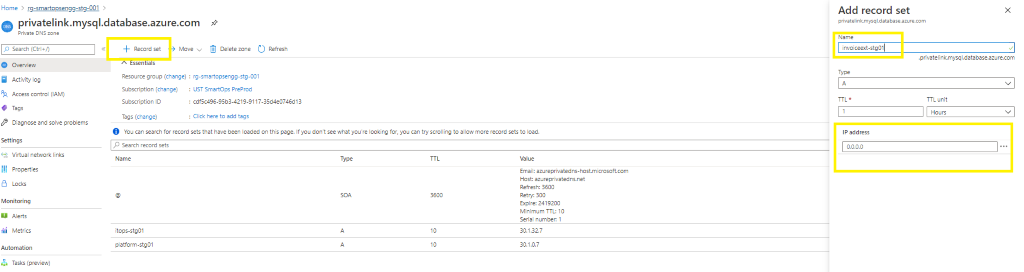
-
When adding new recordset , update the instance name in Name field and add the private endpoint IP in the IP Address field.
-
If the recordset is present but the IP is not associated then Click the record set (Here Azure Key Vault kv-invoiceext-re01)
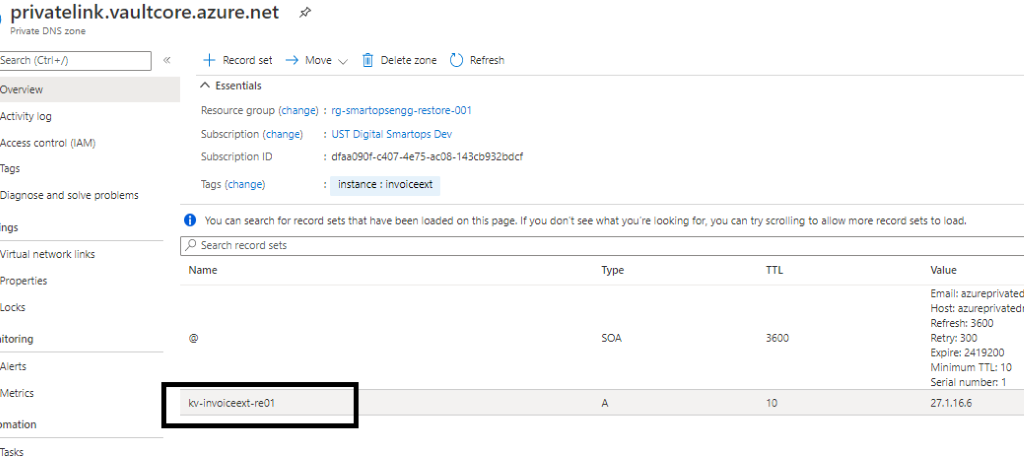
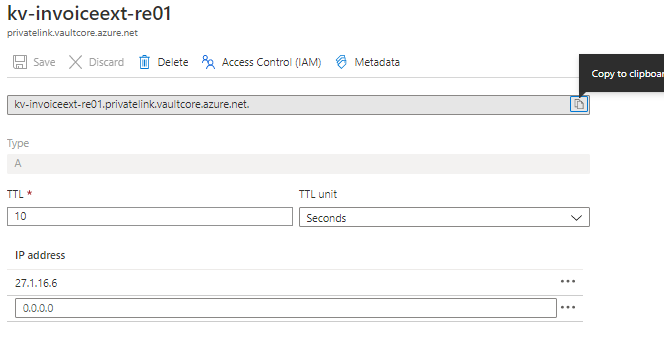
-
Update the Private IP in the ‘IP address’ field
Node pools’ zone redundancy
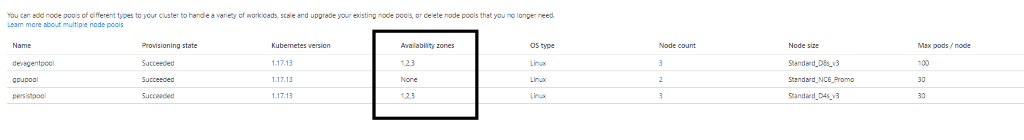
Note: GPU pools does not have zone redundancy enabled since it is not supported in AKS.
FTP Server Creation for Invoice Extraction
Please use below attached script after substituting with required names for vnet , resource group etc.
APPENDIX
Invoice Extraction Azure Resources Asset List
|
Sl No |
Product / PWF |
Asset Name |
SKU / Tier |
Count |
Max Count (where applicable) |
Comments |
|
1 |
Invoice Extraction |
K8s Cluster |
Private Cluster |
1 |
|
Availability Zones have to be enabled and VMs distributed in various zones per node pool |
|
2 |
Invoice Extraction |
Dev Node Pool VMs |
Standard_D8s_v3 |
3 |
4 |
|
|
3 |
Invoice Extraction |
Persist Node Pool VMs |
Standard_D4s_v3 |
3 |
4 |
|
|
4 |
Invoice Extraction |
GPU Node Pool VMs |
Standard_NC6_Promo |
2 |
4 |
|
|
5 |
Invoice Extraction |
OS Disks |
Premium 128GB |
12 |
|
|
|
6 |
Invoice Extraction |
DataDisks - RabbitMQ |
Premium 4GB |
3 |
|
|
|
7 |
Invoice Extraction |
DataDisks - MongoDB |
Premium 32GB |
3 |
|
|
|
8 |
Invoice Extraction |
DataDisks - ElasticSearch Log |
Premium 128GB |
3 |
|
|
|
9 |
Invoice Extraction |
DataDisks - ElasticSearch App |
Premium 32GB |
3 |
|
|
|
10 |
Invoice Extraction |
DataDisks - Prometheus |
Premium 64 GB |
2 |
|
|
|
11 |
Invoice Extraction |
Azure MySQL |
General Purpose, 2 vCore(s), 200 GB(Auto Grow) |
1 |
|
|
|
12 |
Invoice Extraction |
Storage Accounts |
General Purpose v2, ZRS, Hot Tier, Encryption enabled |
2 |
|
|
|
13 |
Invoice Extraction |
KeyVault |
Standard |
1 |
|
|
|
14 |
Invoice Extraction |
Disk Encryption Set |
Customer-managed key |
1 |
|
|
|
15 |
Common |
FTP Server |
Standard B2s (2 vcpus, 4 GiB memory) |
1 |
|
FTP server is used by all products in an environment. Hence kept as common. In Prod this will be per customer |
Invoice Extraction Azure Resources Details
Base Infra

|
Resources |
Description |
|
Application Gateway |
Layer 7 load balancer which manages traffic to applications deployed in Kubernetes cluster |
|
Network Interface |
Network Interface created which is associated with the Bastion VM |
|
Network Security Group |
The network security rules associated with each Product ( SmartOps Platform , ITOps , IE) and maintenance nsg. Bastion VM uses maintenance NSG to access the Kubernetes cluster. |
|
Public IP |
Public IP associated with Application Gateway and Bastion VM |
|
Private DNZ zones |
we have 4 private endpoints per environment. For these 4 private endpoints, we have 3 private DNZ zones. One private zone per Azure blob, Azure Key Vault and Azure MySQL instances. |
|
VM |
Bastion VM which can be used to access the Kubernetes cluster. |
|
VNET |
SmartOps virtual network where all applications are deployed. |
Product Infra
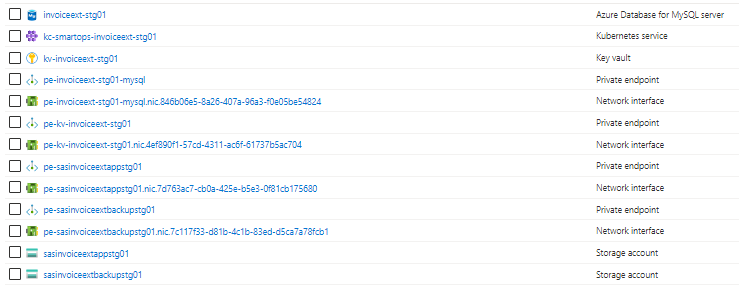
|
Resources |
Description |
|
Azure MySQL |
Managed MySQL instance in Azure Cloud Infrastructure |
|
Kubernetes Service |
Azure Kubernetes Service for Invoice Extraction |
|
Azure Key Vault |
Azure Key vault instance where all Kubernetes secrets are configured |
|
Private endpoints |
Azure private endpoints for Azure Blob, Azure MySQL and Azure Key Vault. Private endpoint enables secure connection to Azure resources. |
|
Network Interface |
Network Interface associated with each private endpoint. |
|
Storage Accounts |
Azure storage account for backup file store and app file store of Invoice Extraction |
Known Issues during Infrastructure deployment and Resolutions.
Issues
|
#1 |
Private Endpoint IP of Azure MySQL, Storage accounts and key vault not associated with respective private link. |
|
#2 |
Azure ARM template deployment failures with status ‘Operation Timed Out’. This can be resolved by redeploying the template. |
|
#3 |
Azure ARM template deployment with status ‘CONFLICT’. This can be resolved by redeploying the template. |
|
#4 |
File copying issues to Storage account blob containers because of firewall policy restricted to ‘all networks’ |
|
#5 |
Kubernetes cluster not able to access key vault because of not setting correct access policies |
|
#6 |
Disk Encryption set not able to get the keys because of not having the Get Wrap and Unwrap permission to key stored in Azure Key Vault. |
|
#7 |
Deployment Engineer not able to access Azure Key vault because of not having required access policies set in Azure Key Vault. |
|
#8 |
Bad Request Status for Storage Account Resources. |
Resolutions
Private Endpoint IP of Azure MySQL, Storage accounts and key vault not associated with respective private link.
Please refer Private Endpoint’s IP Associations
Azure ARM template deployment failures with status ‘Operation Timed Out’. This can be resolved by redeploying the template.
This can occur intermittently because of latency or interruptions with Azure APIs. There are no specific fixes to be applied by Deployment engineer than executing the deployment script again.
Azure ARM template deployment with status ‘CONFLICT’. This can be resolved by redeploying the template.
‘CONFLICT’ during deployments are observed only for NSGs. There are no specific fixes to be applied by Deployment engineer than executing the deployment script again.
File copying issues to Storage account blob containers because of firewall policy restricted to ‘all networks.
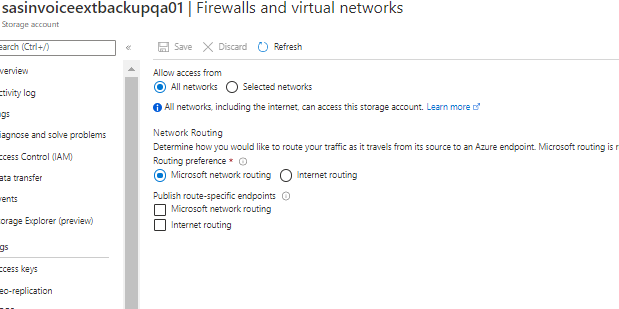
Kubernetes cluster not able to access key vault because of not setting correct access policies
Please refer Azure service principal needs Get permission to Key Vault secrets.
Disk Encryption set not able to get the keys because of not having the Get Wrap and Unwrap permission to key stored in Azure Key Vault.
Please refer Disk Encryption set, storage account, Azure MySQL instance’s Key permissions.
Deployment Engineer not able to access Azure Key vault because of not having required access policies set in Azure Key Vault.
Please refer User’s access to Azure Key Vault instance
Bad Request Status for Storage Account Resources.
Issue
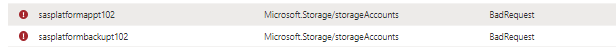
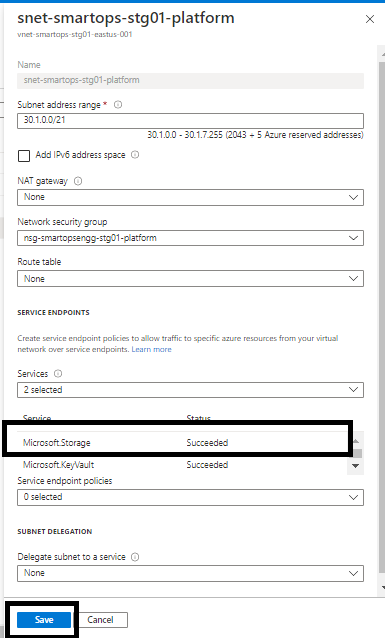
Fix
-
Access the VNET of the resource group and select Subnet. (Here Subnet of SmartOps Platform)
-
Select the service endpoint ‘Microsoft.Storage’ in respective Subnet and click ‘Save’.
FAQ